Report on Lightweight Cryptography
| ✅ Paper Type: Free Essay | ✅ Subject: Computer Science |
| ✅ Wordcount: 1885 words | ✅ Published: 23 Sep 2019 |
Report on Lightweight Cryptography
Abstract:
There are many cryptographic algorithms like AES (Advance Encryption Standard), SHA-256(Secure Hash Algorithm) and RSA/Elliptic Curve, these algorithms work for systems which have reasonable power processing and memory abilities but not for embedded systems and sensor networks. These days most of the people are using low power devices, sensor networks, healthcare and IoT (Internet of Things) for this the traditional algorithms are not supported. Lightweight cryptography methods are proposed to overcome the problems of conventional cryptographic methods. This contains constrains related to physical size, processing requirements and memory boundaries.
Keywords: Lightweight cryptography, security threats, low power devices, algorithms, present and future challenges.
Table of contents
Abstract 2
Introduction 4
Security Threats 4
PerformanceMetrics 5
1. Hardware Specific Metrics 5
2. Software Specific Metrics 5
Algorithms…………………………………………………………………………………………………………………………………………6
Challenges…………………………………………………………………………………………………………………………………………8
Conclusion……………………………………………………………………………………………………………………………………….8
References……………………………………………………………………………………………………………………………………….9
Introduction:
The growth of small computing devices like Radio-Frequency-Identification(RFID) tags, sensor nodes, IoT devices and NIC cards become many. This result has shifted from desktop computers to small devices where security and privacy become more important. in the traditional cryptography methods makes the exchange of security and the performance level which enhanced the change in server and desktop environment. By the change, results become more tough for implementation of the devices with security. So, the lightweight cryptography came into existence to provide solution for resource constrained devices. For lightweight cryptography the main constrains are power requirement and timing. On the other hand, lightweight symmetric cryptography is exclusively established for IoT devices with hash functions. The main goal of this lightweight cryptography is to implement both hardware and software very effectively for low power, embedded and IoT devices [1].
Security threats:
Secure constrained device: in real time the constrained devices are not having the capability of performing complex encryption and decryption quickly. These devices are responsible for attacks like power analysis. Without encryption and decryption, the data is transmitted. This can be reduced by lightweight cryptography by using multiple layer of devices like separating the devices onto septate network.
Secure communication: in low power devices the security challenge is to ensure the communication in network. However, low power devices don’t encrypt the messages before sending over the network. so, to remain data confidential use separate network and isolate the device which helps in secure private communication.
Data privacy and integration: it is important that after transmitting the data over network it should be stored and processed securely. In low power system it is important to implement data privacy which includes formulate sensitive data before it is stored. Data maintenance with legal and regular framework is also an important challenge [2].
Working Mechanism:
Embedded devices have essential limitations like storing of data space, processing the power, memory storage and energy consumption. The cryptographic functionalities use safe environment for software implementation to utilize progressive hardware security. Memory element establish a significant part of size, cost is directly linked to surface of component, speed is related to optimizing the code and the set of instructions are executed quickly which reduces the power consumption. Traditional cryptography focuses on security by ignoring the constrained devices. Lightweight cryptography is mainly focused on constrained devices which have capability of power supply, hardware, software and connectivity [3].
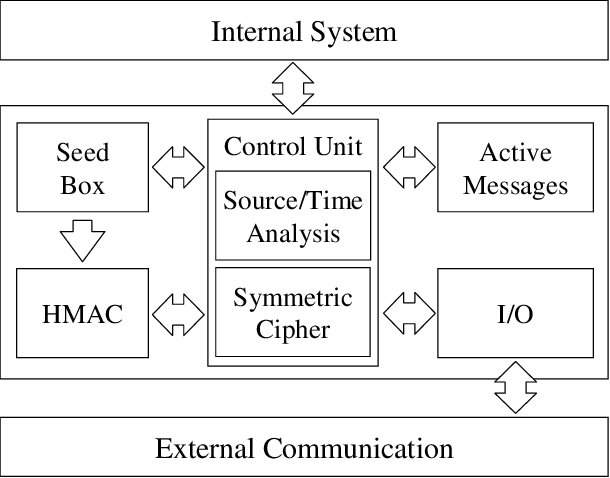
Figure- 1 Working Mechanism
(Source: https://www.garykessler.net)
Performance Metrics
- Hardware Specific Metrics:
The resource requirement for hardware platform are describe as gate area. Gate area is measured in µm2 and implementation depends on technology and standard cell. Gare areas are specified in terms of logic blocks for field-programmable gate arrays (FPGAs) for ASIC applications. FPGAs contains look up tables, flip flops and multiplexer. Logic blocks are deployed differently on different FPGAs so, the count of multiplexer or flip flops depends on FPGAs family or count of output and input bits of look up table. For ASICs 1GE=2 input NAND gate, area in GEs= area in µm2/area of NAND gate.so. GEs hardware implementation is specific to one technology. Low cost RFDI gate count is 1,000 to 10,100 among that 200 to 2,000 are used for security purpose. In this area requirement and power consumption are corelated i.e. minimum area can reduce power consumption [4].
- Software Specific Metrics:
In software application the resource requirement is measure by quantity of registers and quantity of bytes required for Random Access Memory (RAM) and Read Only Memory(ROM). program code is stored in ROM, intermediate values are stored in RAM which can be used for computation. Therefore, small number of register can lower the overhead. The implementation of size and intermediate value consumption and count of bytes for one cycle are best software metrics for lightweight cryptography. The smaller is the best, a framework is planned to estimate the presentations of lightweight block cipher and stream ciphers, the name of the framework is Fair Evaluation of lightweight Cryptographic Systems (FELICS) [5].
Algorithms:
Light weight Block cipher: the light weight block cipher is used to attain performance over AES. In AES 128 bit-block-size uses large keys of size, 128 bits, 192 bits and 256 bits with fixed number of rounds. For instance, it takes 10 portable rounds for 128bits encryption. Similarly, 12 portable rounds for 192 bits, 14 rounds for 256bits. This for IoT consume more memory.so, lightweight block cipher is used with variable block size of 32 or 64 or 128 bits and has a key size of 0-2048 bits by variable number of rounds. For lightweight block cipher, NSA has released SIMON for hardware implementation and SPECK for software implementation [6].
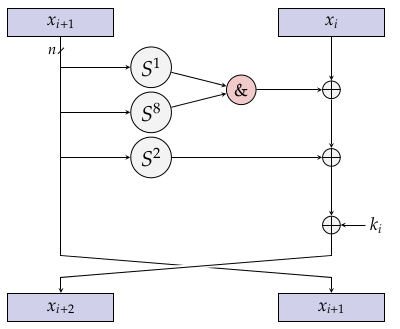
Figure-2 SIMON
Source (www.cryptolux.org)
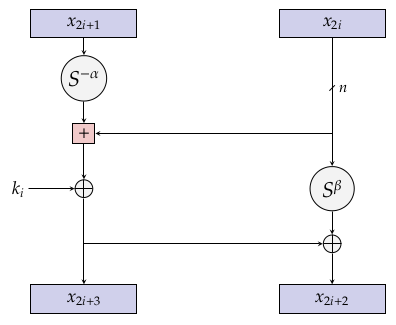
Figure-3 SPECk
Source (www.cryptolux.org)
Lightweight Streaming: this is the first algorithm to show the replacement of AES for lightweight cryptography is PRESENT. It uses small box and potential for small keys. It operates 64 bit with SPN (substitution permutation network) and with AES (Rijndel). We operate it on plain text and apply key then use the rounds by using s- box and p-box. Decryption is same as encryption.

Figure-4 Grain – 80
Source (https://www.cryptolux.org)
The hardware application we use are:
Micky is a type of stream cipher which creates a key stream which is taken from 80-bit key and different length of initialization till 80 bits. The key stream max length is 2^40 bits.
Trivium is type of streaming, which uses 80-bit key for generating 2^64 bits of output.
Grain is a type of streaming cipher which have comparatively low gate count, resource power consumption and memory allocation.it has 80-bit key, two shifts register and non-linear output function [7].
Challenges:
Lightweight cryptography is mainly concentrated on low power like sensors, RFID tags, the Internet of Things (IoT), smart cards, cyber-physical systems, m2m microcontrollers and the smart grid to provide security with fast authentication, identification and data protection. Lightweight cryptography targets IoT end nodes and RFDI tags which can be executed for hardware and software with dissimilar communication technologies. Power is important with the RFDI and energy harvesting devices. Since the power is greatly depends on hardware devices like circuit size or the processor in use. The inspiration of lightweight cryptography is to use low power, low computing resources and low power supply to deliver high security for constrained devices.
Limited RAM and ROM: low energy devices incline to be very minor with high security. For instance, SecureRF provide various cryptography functions like less energy as 0.7%, 5-50% RAM and ROM storage which is essential for elliptic curve methods. moreover, gates essential for hardware applications can be compact by 30% or additional compared with ECC [8].
Partial energy use and limited storage: the constrained devices have low energy usage and storage capacity than bigger machines. For instance, smart android watch has a battery 300 to 500 mAh, the smartphones have 2-3KmAh and 5-12 watts of power supply. When we compare the IoT devices with big machines we can conclude that constrained devices are manufactured for the low power consumption [9].
Conclusion:
From the report we can conclude that lightweight cryptography is designed for resource constrained devices like RFID devices, sensor network, IoT and embedded systems. In case of IoT the data which is collected is used for decision making purpose but, privacy of data gets lost when it is connected to other devices this is the main reason the reputation of IoT gets lost. The size depends on memory element, cost is directly proportional to components, the faster result depends on optimizing the code and power consumption depends on minimizing the quick execution of an instruction set. This all depends on software and hardware metrics which are highly scalable in lightweight cryptography.
Algorithms are designed to overcome the effects of AES. Enormous number of algorithms are proposed like PRESENT, CLEFIA, LED and many more. it has very low estimate power of 5µW and small footprint in hardware 1570 GE. Finally, the lightweight cryptography defines trade-off between lightness and security.
References:
- [1] Saarinen, M.-J.O., and Engels, D.W., A Do-It-All-Cipher for RFID: Design Requirements (Extended Abstract), IACR Cryptology ePrint Archive, 2012, http://eprint.iacr.org/2012/317
- [2] Barker, E., and Roginsky, A., Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths, NIST Special Publication (SP) 800-131A Revision 1, National Institute of Standards and Technology, Gaithersburg, Maryland, November 2015, https://doi.org/10.6028/NIST.SP.800-131Ar1
- [3] Bogdanov, A., Knudsen, L.R., Leander, G., Paar, C., Poschmann, A., Robshaw, M.J. B., Seurin, Y., Vikkelsoe, C.: PRESENT: An Ultra-Lightweight Block Cipher. In:Proceedings of Workshop Cryptographic Hardware and Embedded Systems (CHES 07) (2007)
- [4] ISO, ISO/IEC 29167-1:2014, Information Technology – Automated Identification and Data Capture Techniques – Part 1: Security Services for RFID Air Interfaces, 2014, http://www.iso.org/iso/home/store/catalogue_tc/catalogue_detail.htm?csnumber=61128
- [5] Beaulieu, R., Shors, D., Smith, J., Treatman-Clark, S., Weeks, B., and Wingers, L., The SIMON and SPECK Families of Lightweight Block Ciphers, IACR Cryptology ePrint Archive, 2013, http://eprint.iacr.org/2013/404
- [6] Buchanan WJ, “RC5.” [Internet]. Available from: https://asecuritysite.com/encryption/rc5.
- [7] ISO/IEC 29192-3:2012 – Information technology – Security techniques – Lightweight cryptography – Part 3: stream ciphers.” [Internet]. Available from: https://www.iso.org/standard/56426.html.
- [8] Mouha N. The design space of lightweight cryptography. NIST Light Cryptogr Work. 2015;2015:1–19.
- [9] Yap, H., Khoo, K., Poschmann, A., Henricksen, M.: EPCBC A Block CipherSuitable for Electronic Product Code Encryption. CANS 2011, LNCS, vol. 7092,pp. 76-97. Springer- Verlag Berlin Heidelberg(2011)
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal



